In 2023 alone, 61% of SMBs experienced cyber attacks.
And with more people building apps to scale their businesses, cybercriminals have more opportunities than ever before to exploit your security flaws.
That’s the bad news. So what’s the good news?
Well, cybercriminals aren’t geniuses, and you can keep them at bay by investing in mobile app security. Amongst other things (which we’ll cover in this blog), that means constantly monitoring, maintaining and testing your mobile app.
For reference, I’ve been developing and maintaining a suite of information security policies and protocols for over 11 years, and the advice I give below draws on all of that experience.
To learn more about common vulnerabilities and how to reinforce your app security, keep scrolling 👇
What is mobile application security?
Mobile application security refers to the protocols and methodologies used to protect mobile apps and the data they handle from unauthorised access and cyber-attacks. Effective mobile app security identifies your app’s vulnerabilities and fixes them before data is compromised. It’s also conscious of both existing and emerging threats.
The need for mobile app security
According to a report, there’s a 32% chance that even a new mobile app has at least one security loophole, and by the time it’s 5 years old this number reaches 70%. An app with neglected cybersecurity is a sitting duck.
Yet only 14% of SMBs are prepared for cyber attacks. There’s a growing need for businesses to implement robust protocols and do regular security audits to mitigate these risks.
Another important reason for having robust mobile app security is the increasing adoption of in-app transactions. Lots of apps use monetization techniques like in-app purchases, for which users need to provide their banking details to the app.
A cyber attack could lead to data leakage for thousands of users putting their finances — and the reputation of the app — at risk.
What are common security risks in mobile apps?
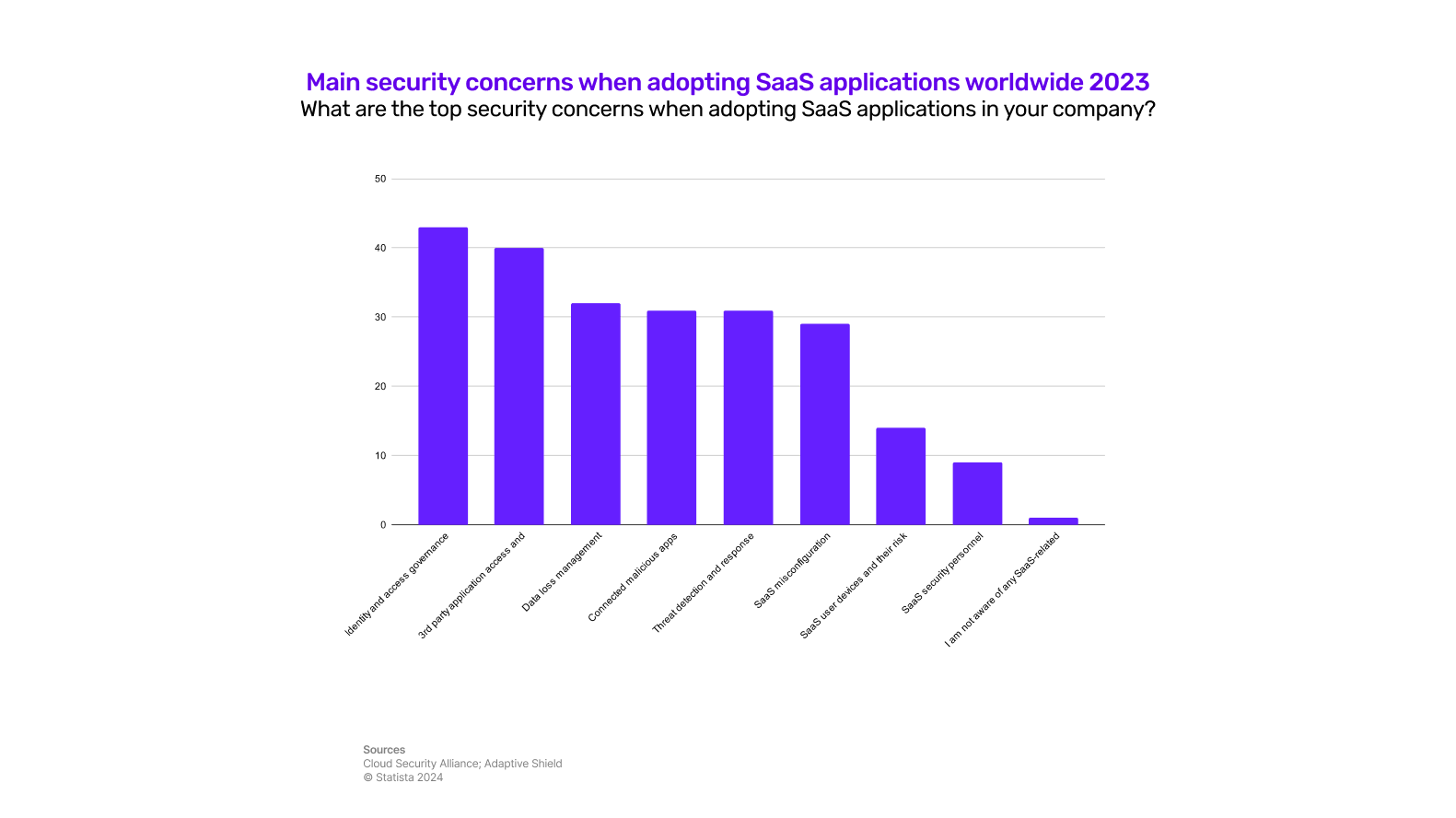
Now that you know the importance of mobile application security, let’s move to the common security risks that you can face while creating your app from scratch 👇
1 - Access management
Identity and access management is a significant concern, with 43% of respondents to the survey above considering it as the main security risk. This is because weak access controls can allow hackers to gain entry into the app’s systems and access sensitive data.
But with the right approach, you can minimise risks and keep your app safe. For instance, using role-based access control ensures that users get limited access appropriate to their roles. By limiting access to only what's necessary for each user's tasks, you can minimise the potential impact of security breaches.
Further, when it comes to third parties, make sure their access is in line with the services they provide. This helps you prevent misuse of access and lowers the chances of data breaches.
2 - Third-party integrations
Third-party services or APIs can introduce potential vulnerabilities into your app's ecosystem, as these services may not meet the same security standards as your app. They might lack in terms of data transmission, authentication, or data protection.
Also, relying on third-party services makes your app dependent on them. Any security breach in them can directly impact your app and users. According to Statista, 40% of people believe third-party applications and their level of permissions are a security concern for them.
To mitigate these risks, you must provide them with the minimum access required for their functionality.
Plus, carefully vet third-party service providers before integration. Make sure they have proper security measures and certifications in place. For example, ISO 27001 establishes information security management, SOC2 assesses an organisation’s controls and PCI DSS aims at securing payment card data.
3 - Data loss management
According to Statista, data loss management is considered the third biggest security concern for an app. The loss of sensitive information can have significant consequences for both the users and the app.
To mitigate this risk, you should:
- Establish a policy that limits data access by role
- Create alerts for excessive data downloads
- Create alerts for excessive access to data
- Use password protection for externally shared data
- Have an expiration date for access to externally shared data
- Run employee training and awareness programs
4 - Insecure code
According to Gartner Security, 90% of all vulnerabilities are located inside the app code. This means that insecure coding makes your app most vulnerable to attacks.
While automated tools can detect flaws in your code like memory leaks and buffer overflows, they may miss some security threats and aren’t enough by themselves. You need to do manual app testing for a comprehensive review and follow secure coding practices so that it doesn't lead to vulnerable code in the first place.
5 - Threat detection and response
Ineffective threat detection and response mechanisms can result in delayed identification and mitigation of security threats. Around 30% of respondents consider it a top security concern for mobile applications.
To get ahead of bad actors, you need to identify vulnerabilities so you can prioritise remediation efforts. If not done correctly, they can take advantage of them using many tactics like:
- Phishing – emails sent to trick employees into providing their credentials or downloading malicious code
- Malware – software designed to corrupt computers or collect information
- Ransomware – a threat to make private data public for a ransom
- Code injection – tampering app’s source code by injecting malicious code into it
- Identity-based threats – theft of user credentials and using it to gain access organisational data
To mitigate these risks, you need to have a robust detection and response mechanism tailored to your organisation’s needs and risk profile. After detecting a credible cyber threat, you need to have a fast threat response to contain the attack and also make sure this kind of attack doesn’t happen again.
Benefits of keeping mobile apps secure
Most of the benefits of mobile app security are preventing bad things from happening to your business and customers. But there are some additional upsides to keeping your mobile apps secure. Let’s check them out 👇
1 - Reduced costs
Cyber attacks and data breaches can be costly for your business. First, you’ll have direct implications like fines for failing to protect sensitive data, as well as legal fees for lawsuits from affected users.
Second, there are indirect costs like damage to brand reputation and users seeking alternatives.
Mobile app security helps you prevent these incidents and save the financial costs associated with them.
2 - Financial data remains secure
Most apps ask for credit card details, home addresses, order lists and other financial data from users to facilitate transactions.
So, if you’re running an ecommerce store, a food delivery business or any other app, you need to make sure that this financial data is secure from unauthorised access or exploitation.
Additionally, secure financial data facilitates open banking. Open banking is a financial model in which two parties share banking data through APIs. This enables apps to offer enhanced financial services like personalised budgeting, real-time transaction monitoring, and seamless funds transfer across accounts.
3 - Regulatory compliance
Every country has its own data protection laws, and having legal trouble is the last thing you want for your app. Failure to comply with regulatory requirements in your region can result in severe consequences, including legal penalties, lawsuits, sanctions, and even suspension or removal of your app from app stores.
Keeping your app secure helps you avoid hefty fines and legal trouble while running your app.
Additionally, compliance with regulations helps your app enter new markets and expand your user base by ensuring that it meets the legal requirements of those regions.
4 - Enhanced user trust
The level of trust a user has in your app directly impacts the success of your business. When users feel confident that their personal and financial information is protected, they’re more likely to engage with your app and share positive reviews and ratings on app stores.
By implementing robust security measures, you demonstrate your commitment to protecting user privacy and security, increasing confidence in your user base, and building a positive reputation for your app.
5 - Competitive advantage
Enhanced security gives your app a competitive edge and helps it stand tall in the market. This is because when users know that their data is safe and their privacy is protected, they’re more likely to choose you over competitors.
A secure app attracts new users and at the same time, retains the existing ones, leading to increased loyalty.
Want to start your app project with us?
Book a demoSpeak with one of our product experts today.
By proceeding you agree to Builder.ai’s privacy policy and terms and conditions

Best practices to boost mobile app security
Having robust mobile app security is a no-brainer. Let’s dive into the best practices you should follow to give it a boost. 👇
1 - Develop your app with secure code
Embrace secure coding practices to protect your app. Writing and including the right code from the initial building stages makes sure your app is more secure when it comes to launching.
Malicious cyber attacks like SQL injection can be easily prevented with strong authentication protocols and initial prevention code from the start.
Wait! – what’s an SQL injection? It’s a code-based vulnerability that allows an attacker to read and access sensitive data from your database.
One of the best ways to check if your sensitive information is safe is to perform penetration testing. Penetration testing is a proactive approach where you perform simulated or mock attacks to reveal potential vulnerabilities and risks.
They’re essentially spot-checks to detect loopholes in your system. Especially as these small loopholes can become huge threats once your app grows. It’s good practice to try and test your app with randomly generated scenarios to stay up to date on your security health.
Learn more aboutmobile app testing👈
2 - Have ongoing compliance monitoring
One of the best practices to protect your app is by having ongoing compliance monitoring. Most industries need your app to follow regulations for data storage and protection. For instance, if you operate in the ecommerce industry, you need to comply with the General Data Protection Regulation (GDPR).
Implementing ongoing compliance monitoring practices ensures that your app consistently meets these regulatory requirements. This involves regularly assessing your app's data handling processes and access controls to make sure they align with industry standards.
3 - Secured authentication
Tactics such as multifactor and biometric authentication significantly enhance your app security. These enhancements add an extra layer of protection to your app beyond traditional password-based systems.
For instance, requiring users to verify their identity through OTP, fingerprint or facial recognition in addition to entering a password makes it much harder for unauthorised users to gain access to sensitive information.
To further increase the security of your app, you can also use passkeys, which are unique PINs or patterns known only to the user. They provide a seamless sign-in experience and users don’t have to remember usernames and passwords.
This means even if a hacker manages to obtain a user's password, they'd still need to pass additional authentication steps, reducing the likelihood of unauthorised access.
4 - Implement access controls
Implementing access controls ensures that users can only perform actions based on their assigned roles.
For example, for a healthcare app, you can assign roles such as “Doctor”, “Pharmacy” and “Patient”, each having distinct access privileges. Here, doctors may have full access to patient records and treatment plans, while the pharmacy may have access to past prescriptions. Patients, on the other hand, would only have access to their own health information.
By restricting access to sensitive data based on user roles or attributes, you can maintain confidentiality and integrity, ultimately enhancing your app's overall security posture.
5 - Enforce session logout
Automatically log your users out from your app after a period of inactivity. This reduces the risk of unauthorised access to sensitive data and can prevent potential security breaches.
For instance, in banking or payments apps, session logout can be particularly useful even if the mobile device is stolen or lost.
Although your users need to reauthenticate whenever they want to access the app, you can enhance the overall security of your app and instil confidence among your users.
6 - Ask for minimal app permissions
Permissions give mobile applications the necessary access to device resources. However, unnecessary permissions can put your users at risk.
Keep app permissions to a minimum and ensure that your app asks for what it really needs for functioning properly.
Additionally, regularly review and update permission settings to maintain a secure environment for your users and protect their data from misuse.
7 - Monitor your app thoroughly
Monitoring tools can be implemented to detect any suspicious activity related to user accounts or transactions. Investing in appropriate monitoring solutions can aid in tracking activities across both internal infrastructure components as well as online channels connected through API gateways. Some cyber-security tools include:
- Microsoft Azure – Azure provides several monitoring tools that observe operations and detect anomalous behaviour; these tools can detect threats at different levels and report security issues
- Snyk – a developer security platform that allows you to scan, prioritise and fix security vulnerabilities in your code, open source dependencies, container images, and Infrastructure as Code (IaC) configurations
- Open Web Application Security Project (OWASP) – one of the world's most popular free security tools helping protect web applications from cyber attacks
8 - Regular app maintenance and security updates
Keeping your app secure isn't a one-time process. As new threats emerge each day, you need to regularly maintain your app. This includes updating your app with the latest security patches and fixes as soon as they become available.
By staying on top of maintenance and security updates, you can ensure that your app remains protected against evolving threats and vulnerabilities.
Additionally, you need to conduct regular security audits to identify any potential weaknesses in your mobile application security so you can address them proactively.
How does Builder.ai keep your apps secure?
Builder.ai has a robust, cloud-based security infrastructure. This is divided between Microsoft Azure and AWS (Amazon Web Services), ensuring high availability, scalability, and reliability for our services.
Who has access?
Safeguarding our systems and those of our customers and partners is paramount. We operate on a Zero Trust Model, meaning we grant access only when necessary and on a need-to-know basis.
Here's how we manage access:
- Strict controls – we tightly regulate access to all internal services and products
- Least-privilege basis – we follow the principle of least privilege, granting access only to the services required
- Identity access management (IAM) – we use IAM to control access to the cloud providers we use; this ensures that only authorised individuals and systems can interact with the essential services they need
Where do we store data?
Customer data is securely stored in data centres operated by our cloud service providers. These data centres adhere to strict security standards and compliance certifications such as SOC 2,ISO 27001andGDPR.
What do we do to keep data secure?
Builder.ai is committed to protecting the privacy of customer data and adheres to relevant data protection regulations such as GDPR and CCPA (where applicable). We have comprehensive privacy policies in place.
We subscribe to the AWS and Azure Well-Architected frameworks.
These include:
- Least privilege – we ensure that users have only the necessary access to perform their tasks, enhancing security
- Real-time monitoring – we monitor activities constantly and receive alerts immediately to detect and respond to any suspicious behaviour
- Layered security – we implement security measures at every level to provide comprehensive protection against threats
- Automated best practices – we automate security protocols by embedding them into our code, ensuring consistency and efficiency
- Data protection – we secure data both in transit and at rest to prevent unauthorised access or breaches
- Minimised data access – we limit direct access to data, reducing the risk of exposure to unauthorised individuals
- Incident preparedness – we have a robust incident management process in place to effectively handle security incidents when they occur
You can find out more about our security policy here 👈
Conclusion
As a business, it's up to you to keep operating systems, libraries and frameworks up-to-date for reliable protection against modern cyber attack techniques.
A trusty maintenance package will defend your app and your customers from phishing campaigns or malware infiltrations, making everyone feel a lot safer.
Builder.ai offers an entire maintenance package, Studio One, that incorporates the latest security and safety measures into every app we build. Our systems are constantly looking out for potential bugs, essential updates and performance optimisation to improve and protect your app's lifecycle.
Studio One comes into play the moment you start building an app with us, making sure your app is future-proofed from day one. Plus, our apps are rigorously tested throughout app development.
Want to start your app project with us?
Book a demoSpeak with one of our product experts today.
By proceeding you agree to Builder.ai’s privacy policy and terms and conditions

Nico is a DPO and Information Security Officer at Builder.ai. He has over 11 years of experience developing and maintaining a suite of information security policies and protocols. He excels at a range of privacy, security, compliance, IT audit, risk and data protection skills and has worked in many industries like ecommerce, travel and financial services.








 Facebook
Facebook X
X LinkedIn
LinkedIn YouTube
YouTube Instagram
Instagram RSS
RSS


