App security continues to be a top priority for businesses of all sizes. With hackers finding new ways to exploit vulnerabilities in your app, merely having app security measures in place isn’t enough.
You need to make sure that these systems are not only robust but also regularly assessed to identify and mitigate potential threats.
This is where conducting a comprehensive application security assessment becomes invaluable.
An app security assessment is a proactive approach that helps you find out your app’s potential weaknesses before they become a problem. Without regular security assessments, you’re essentially missing out on a chance to stop hacks and are left to react to breaches, which can have more severe consequences in terms of time and resources.
In this blog, I’ll talk about why app security assessments are important and provide you with an 11-step guide so that your app remains protected. In the end, I’ll also provide you with a sure-fire way to keep your app secure so that you don’t have to worry about it ever again.
Let’s dive in 👇
What is an app security assessment?
An app security assessment is a comprehensive evaluation aimed at identifying and fixing potential security vulnerabilities within an application. The primary benefit of this holistic approach is comprehensive protection, addressing a wide range of potential threats and providing a more robust security posture.
App security assessments account for both internal and external security risks. To cover internal security risks, it includes penetration testing, configuration review and authentication and authorisation testing. And to account for external security risks, it includes data protection assessments and scrutinises vendors and third-party management.
Why are app security assessments important?
Conducting regular security assessments should be a critical part of your organisation's cybersecurity strategy. The importance of this process is underscored by alarming statistics that highlight the prevalent security risks and potential financial repercussions associated with security incidents.
For instance, in 2023 alone, 61% of SMBs experienced cyberattacks. The global average cost of a data breach? A staggering $4.45 million. Moreover, the process of identifying and containing a breach isn't only expensive but also time-consuming, with an average duration of almost 204 days (7 months).
Beyond providing security, app security assessments have additional benefits:
- Staying complaint: they help you meet industry rules and regulations
- Protection of data: they help keep sensitive data safe
- Cost savings: fixing issues is cheaper than dealing with a breach later
- Building trust: shows you care about security of your user’s data
When and who should conduct app security assessments?
To conduct security assessments, you need to make sure that the right people conduct them at the right times to keep your app safe 👇
When should you conduct security assessments?
Integrating security from the beginning of the app development process is essential. By performing security assessments early in the development stages, vulnerabilities can be identified and fixed before the app is even deployed, significantly reducing potential risks.
Once your app is launched, you should continue these assessments regularly. At a minimum, security assessments should be conducted annually. However, it's best practice to perform these assessments after every major release to address any new security challenges that may arise from recent changes or updates.
Simply put, security assessments should be an integral part of your software development lifecycle (SDLC).
Who should conduct security assessments?
While the app owner is responsible for their app's security, I’d recommend working with security experts and third-party firms that offer security services. These experts specialise in identifying and mitigating security risks and bring a wealth of experience from working across different industries.
Their expertise can provide you with a deeper insight into potential security threats and offer advanced solutions to protect your app against emerging security challenges.
What is the difference between security assessment and security audit?
For those outside the cybersecurity industry, the terminology of data security issues can be overwhelming. Let’s understand this with an analogy.
If a security assessment makes sure that your home alarm system is installed, then a security audit confirms that it not only exists but also functions correctly when triggered.
An application security audit offers a formal, comprehensive review of your entire security framework. This includes examining your physical infrastructure (such as networks and firewalls) and evaluating policies and operational procedures to make sure they comply with established security standards.
11 app security assessment steps
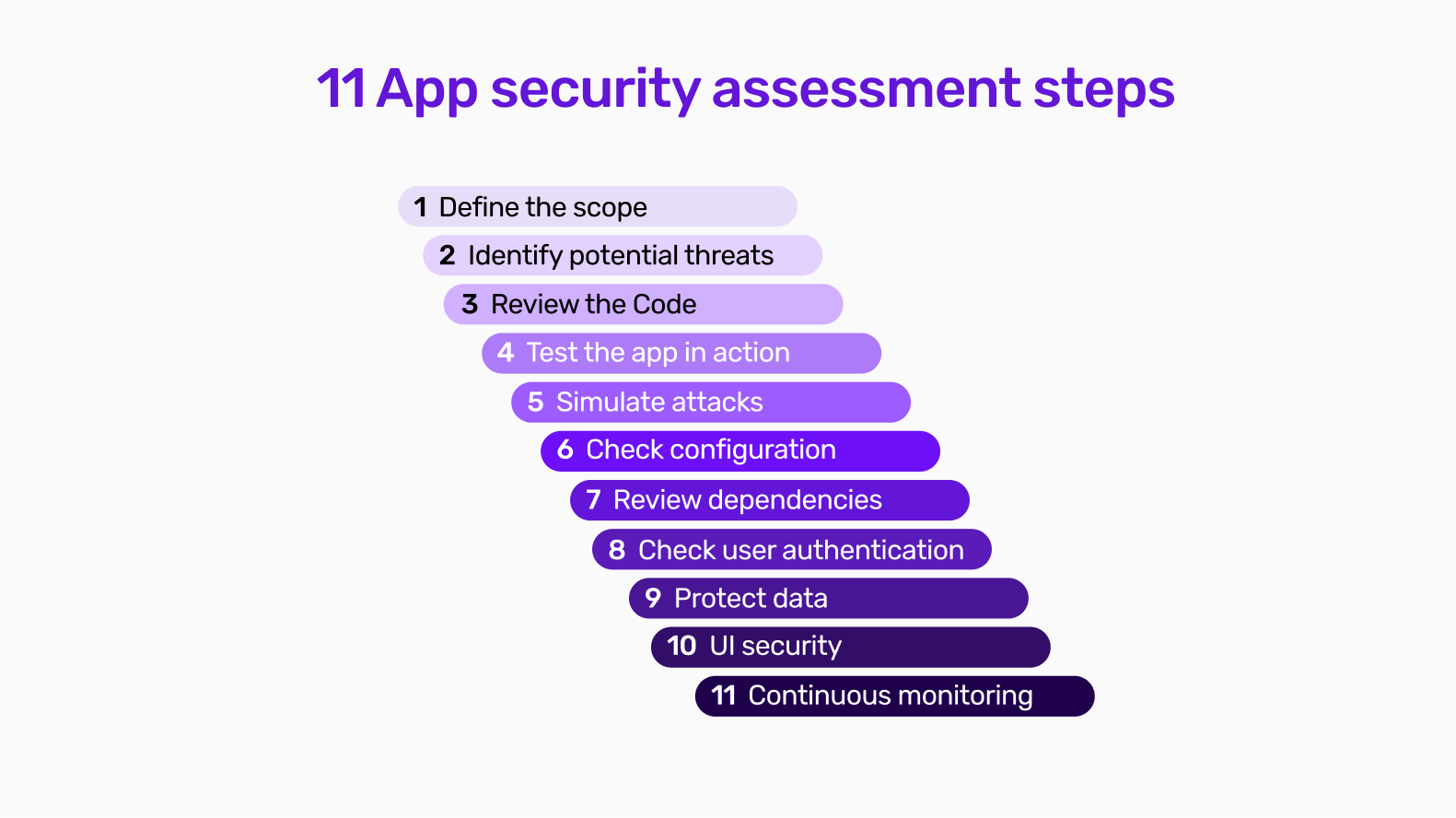
App security assessment involves a structured approach to identify and mitigate vulnerabilities. You can do this by following established frameworks like the OWASP testing guide or NIST application security guideline to ensure a comprehensive evaluation.
Let’s dive into a detailed explanation of what each step entails 👇
Step 1 - Define the scope
The first step in an application security assessment is defining the scope.
Begin by determining which parts of the app and its related systems will be checked. This includes identifying specific components, systems and data that are crucial to your organisation.
This is important because it allows you to focus on critical areas and allocate resources effectively for a thorough assessment.
Step 2 - Identify potential threats
Once you’ve decided which parts of the app will be checked, start identifying the critical components and data that need protection, such as user information, financial data and intellectual property.
Think about what could potentially go wrong, like hackers stealing data, unauthorised access and malware attacks. This step helps you in understanding the threat landscape and prioritising security measures.
Step 3 - Code review
According to Gartner Security, 90% of all vulnerabilities are located inside the app code. Therefore, once you’ve identified potential threats, conduct a thorough code review to find any obvious security issues.
This step should involve both manual inspection by experienced developers and automated inspection by sophisticated static analysis tools to ensure that both common and less obvious code vulnerabilities are identified.
These tools can help identify vulnerabilities such as SQL injection, XSS and insecure configurations, enhancing the efficiency and coverage of the review.
Step 4 - Test app in action
Next up, you need to test your app in action. To do that, you can do runtime security testing. This means checking the app while it's running to find problems that may not be seen in the source code, like memory leaks and unsafe data handling.
Use automated scanners to detect vulnerabilities that might not be evident during static code analysis. This includes stress testing the application to see how it handles unexpected or heavy loads, which can often reveal hidden issues.
Learn more about mobile app testing 👈
Step 5 - Simulate attacks
In this step, you conduct penetration testing where you act like a hacker and try to break into your app. It’s a great way to exploit vulnerabilities and test the app's resilience to real-world threats.
Additionally, you should include tests for privilege escalation to see if higher access levels can be broken within the app to find weaknesses.
Step 6 - Configuration review
In this step, you make sure that the servers and systems supporting the app are set up securely. Here, you need to verify that the application’s settings adhere to security best practices to prevent exploitable misconfigurations. This includes reviewing server security settings, database configurations and any cloud-based resources involved in the application’s operation.
You also need to check that the app's settings are safe and do what you need to keep them safe, like setting up strong password rules and making encryption available.
Step 7 - Review dependencies
The seventh step of application security assessment is to check any external code the app uses for known security issues. Evaluate the security of third-party libraries, frameworks and components integrated into your app.
Here, it's also good to check the security of any external services or APIs your app uses to make sure they don't introduce vulnerabilities.
Step 8 - User authentication
According to Statista, 43% believe that user authentication and access management is a common security risk.
This step checks that the login system in your app is safe and protects user credentials. Verify that authentication mechanisms, such as multi-factor authentication, are implemented correctly to protect user accounts.
You should also verify that users can only access what they’re supposed to. Make sure that role-based access controls are enforced and that sensitive operations are properly restricted.
Step 9 - Data protection
After user authentication comes data protection. In this step, you make sure your app’s sensitive data is encrypted when stored and transmitted.
To do that, you need to implement data encryption both at rest and in transit to protect it from unauthorised access.
You also need to review how your app data is stored to make sure it complies with data protection regulations such as GDPR and CCPA.
Step 10 - User interface security
You can ensure user interface (UI) security in 2 ways:
- Input validation - Check that user inputs are properly validated to prevent attacks. Implement input validation to prevent injection attacks and ensure that user inputs are sanitised.
- Error handling - Ensure that error messages don’t reveal sensitive information. Proper error handling can prevent attackers from gaining insights into the application’s internal workings.
Step 11 - Continuous monitoring and maintenance
The final step in conducting an application security assessment is to keep an eye on the app's security regularly to maintain a strong security posture.
To do this, implement continuous monitoring and app maintenance to detect and respond to new threats promptly. Additionally, keep updating security measures regularly to keep up with evolving risks and ensuring ongoing protection.
Conclusion
As a business, you need to remember that preventing a security breach will always cost much less than fixing one.
But the steps above indicate that conducting an app security assessment is easier said than done. It requires a complete understanding of potential threats, meticulous code review, rigorous testing and continuous monitoring. Therefore, you need to partner with experienced security professionals to ensure your app is fully protected.
With Builder.ai, you don't need to worry about security patches and backup management. We take full responsibility for these critical aspects, ensuring that your app’s security is continuously monitored and updated. This allows you to focus on what truly matters—growing your business.
If that sounds good, click on the banner below and learn more about how Builder.ai handles the complexities of app security and keeps your app safe 👇
Want to start your app project with us?
Book a demoSpeak with one of our product experts today.
By proceeding you agree to Builder.ai’s privacy policy and terms and conditions

Nico is a DPO and Information Security Officer at Builder.ai. He has over 11 years of experience developing and maintaining a suite of information security policies and protocols. He excels at a range of privacy, security, compliance, IT audit, risk and data protection skills and has worked in many industries like ecommerce, travel and financial services.








 Facebook
Facebook X
X LinkedIn
LinkedIn YouTube
YouTube Instagram
Instagram RSS
RSS


